NSA Goal Is ‘Total Population Control’
Here are four clips by former National Security Agency (NSA) officer Bill Binney that reveal the Big Brother global surveillance system tracking every electronic move we make. He’s been speaking out for the past 20 years, and we, the public, just allow it, thereby giving our consent by stealth.
Although, it could be propaganda (perhaps to get truth-seekers researching this, instead of the far more nefarious programs really going on) i.e. anything disclosed in mainstream news, such as BBC News, The Guardian and The Washington Post should be taken with a truckload of salt, as nothing is “revealed to the public” unless it’s deliberately disseminated. (01) (02) (03) (04)
(Unless the crack-down on the mainstream media reporting anything independently only started after 2015, which I highly doubt, albeit we know the censorship-hammer and propaganda-ramped-up exponentially in the years preceding the plandemic, but I think the media has always been captured)… and this particular type of disclosure feels so familiar to recent events in Russia i.e. deliberate propaganda disseminated throughout the media, even though they are all actually on the same side
However, the other aspect is revealing things to the public is also a way they gain “our consent“. They reveal it, and the stupid, helpless masses don’t do anything about it anyway, thereby we are “consenting” by way of allowing it. i.e. the deliberate disclosure of the Balenciaga child-sex bondage clothing scandal. Did the public do anything? Nope, a little outrage, a mainstream campaign to apologize, then back to sleep, as we are perfectly conditioned to do. (05) (06)
Big Brother Surveillance is watching, we should be outraged, but we turn it into an entertainment show on TV.
Whistleblower: NSA Goal Is ‘Total Population Control’
14 Apr 2020 YouTube (15min) Rumble-Mirror (4min) | Telegram
William Binney worked for the National Security Agency as a code-breaker for more than 30 years. At a recent conference, he said their ultimate goal is total population control.
In September 2002, he, along with J. Kirk Wiebe and Edward Loomis, asked the U.S. Defense Department Inspector General (DoD IG) to investigate the NSA for allegedly wasting “millions and millions of dollars” on TRAILBLAZER, a system intended to analyze mass collection of data carried on communications networks such as the Internet. Binney had been one of the inventors of an alternative system, THINTHREAD, which was shelved when Trailblazer was chosen instead. (07)
Clip (38:10-39:08) from 2017 How the NSA tracks you (1hr) (17)
Their agenda is the one that’s driving them, and that’s one that means money, power, and control, and the way you get that is to take in data on everybody on the planet.
That gives you that power.
Then you can swindle money because you can let things happen because of the way you’re doing business, and that’s more justification to get more money; it’s like a swindle. I called the terrorism thing, “trading privacy for security”, a lie from the beginning.
That’s just the way they swindled everybody: they take in all the data, and more people get killed. As people get killed when they don’t stop a terrorism attack, they say they need more money, more people, and more bureaucracy to stop it.
Clip (8:02-15:46) from 2017 How the NSA tracks you (1hr) (18)
Cable Program
These are the ways that they basically collect data:
First, they use the corporations that run the fiber optic lines.
- Corporate
- Foreign
- Unilateral
- RAMPART-M (undersea cables, since 1986) (21)
- RAMPART-T (ClanSIG) (land-based cables, with CIA, since 1991)
- RAMPART-I/X (Iraq/Afghanistan, since 2001)
- DANCINGOASIS (since 2011) (22)
- MYSTIC, etc.
- If that doesn’t work, they’ll tap the line anywhere they can get to it, and they won’t even know it. The governments and the communications companies won’t even know they’re tapped. So that’s how they get into it.
Then they get into the fiber lines.
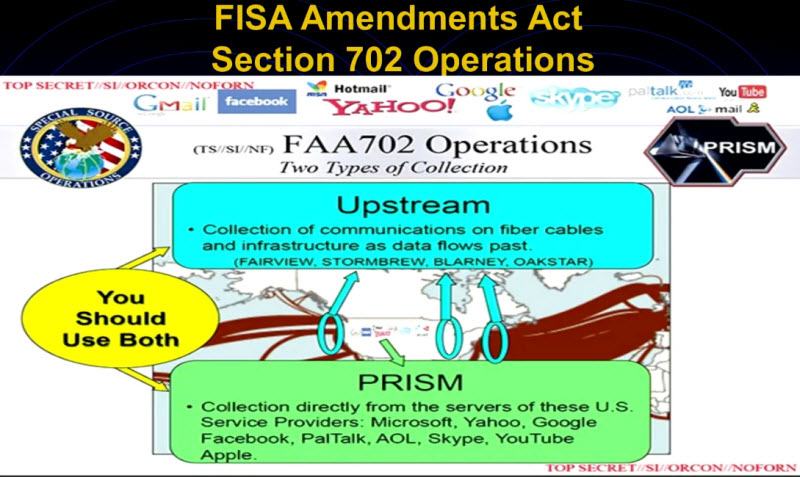
- This is the PRISM program.
- It’s where they have all the companies involved (Google, Facebook, Yahoo!, Hotmail, Skype, AOL, YouTube, Apple, PalTalk, etc.) (23)
- First thing published out of the Edward Snowden material.
- PRISM is really the minor program
The major program is Upstream.
- Collection of communications on fiber cables and infrastructure as data flows past (FAIRVIEW, STORMBREW, BLARNEY, OAKSTAR)
- That’s where they have the fiber optic taps on hundreds of places around the world. That’s where they’re collecting off the fiber line all the data and storing it.
- PRISM was simply their way of putting out something where Congress and the courts could look at it and see we’re abiding by the law.
- When an upstream, they were taking everything off the line.
Also, the MUSCULAR program was a parallel one, which basically for Yahoo and Google and a couple others. They unilaterally tapped lines between their data centers when they transferred data to back it up and so on. They got everything they had and they didn’t know it. So that was the MUSCULAR program from those companies plus the upstream is really the main one, and PRISM was only one small input to the data that NSA was collecting.
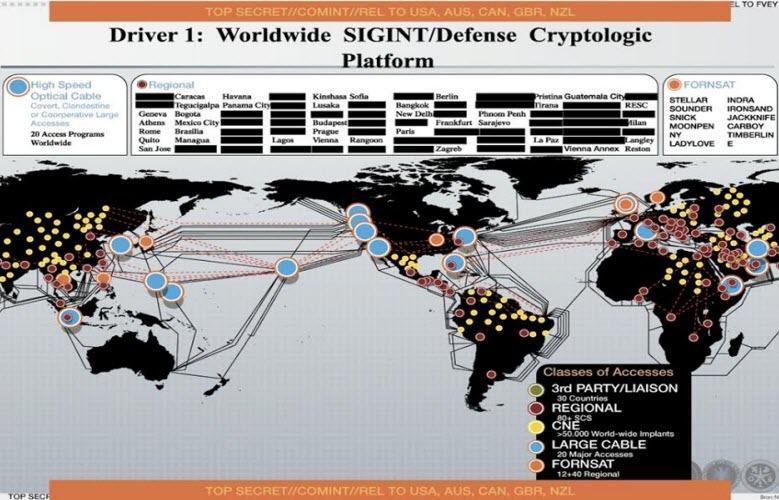
Worldwide, these are the kinds of things they have.
The real big one is over there at CNE, Computer Network Exploitation. (24)
- That’s where they’re implanting either with hardware or software, both, into switches and servers around the world.
- The yellow dots on the map give some indication of where NSA has placed over 50.000 implants in computer networks as part of it’s Computer Network Exploitation (CNE) operations. (25)
- And they can make them do anything they want because they own them.
- So if you send data anywhere through those switches or servers and there’s tens of thousands of them in the world, they basically own the network. They have access to it and they get it.
FORNSAT (Foreign Satellite interception) Stations:
- The orange dots on the map represent locations where there are stations for intercepting the signals of foreign communication satellites. (26)
- STELLAR – Geraldton (Australia)
- IRONSAND – Waihopai (New Zealand)
- MOONPENNY – Menwith Hill (Great Britain)
- INDRA – Khon Kuen (Thailand)
- LADYLOVE – Misawa (Japan)
- TIMBERLINE – Sugar Grove (US)
- JACKKNIFE – Yakima (US)
- SOUNDER – Ayios Nikolaos (Cyprus)
- SNICK – near Seeb (Oman)
- CARBOY (Bude)
So all of that is feeding another program that they call Treasure Map.
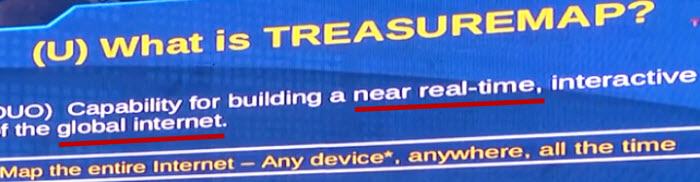
“We want to know where everything is in the world every minute of the day.”
- So it’s not just collecting what you’re saying (encrypted or not), it’s also monitoring where you are when you do it.
- Everything they collect then maps to a physical network and then logical networks who’s communicating across them.
- That maps to equipment, which in turn, maps to people, and that’s how they follow everybody.
Random Slaughter
- This is also when you have cell phones, for example, how they take GPS and use the drones to target people.
- So I think Jacob Applebaum was one who said “NSA tracks them and CIA whacks them.”. (27)
- And the way they do that, and there’s 1.2 million people on the drone list according to the last number I saw. I mean, that’s crazy.
- They aren’t verifying who they’re hitting. They’re just killing people all the time. This is insane.
- I call that program “Random Slaughter”, because that’s about what it is.
- They’re doing stupid stuff. It’s hurting a lot of people.
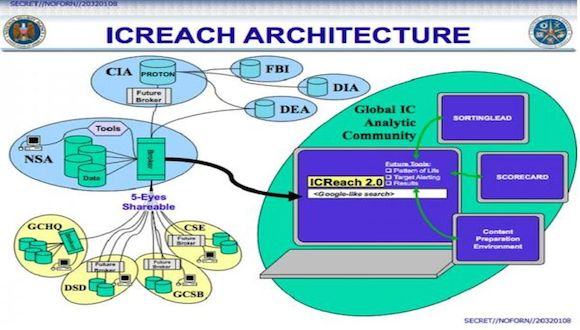
All the material they collect from all the sources goes back into these programs back inside NSA — over here in that rectangle over there, basically a square evidently.
- Worst colour palette ever. Let me guide you from my larger image copy in case you can’t read the text.
- Top: Gmail, Facebook, Hotmail, Yahoo!, Google, Apple, Skype, PalTalk, YouTube, AOL
- From Left to Right: Data Provider (Yahoo, Google, etc.) > FBI DITU
- FBI DITU > FBI / Dual Route Upon Request
- FBI DITU > CIA / Dual Route Upon Request
- NSA
- FBI DITU > PRINTAURA S3532 > TRAFFICTHIEF (28) (29) (30)
- These programs, MAINWAY and MARINA, (graphs of social networks)… (34) (35)
- There are basically two systems they’re following:
- public switch telephone network, which is all the phones — fixed, mobile, satellite, any kind of phone;
- and all the content data then goes into NUCLEON,
- and it’s indexed up there by the MARINA program
- So that when they want to see who did what, they have an index all to everything ever said in their database.
This was the whole design I left them and they haven’t changed a damn thing in 16 years. So that’s real “progress” for ya.
- One of the things to look over here on the slide is that both CIA and the FBI through the FBI Center in Quantico, Virginia, have direct access into these databases and the entire graph.
Not only that, but they also use that for police around the world.
So it’s a straight violation of everything. All this data is collected without warrants. So it’s a basic violation of the rights of every human in a court of law. That’s what they’re using.
And these are other people who have access to it.
- The Five Eyes (FVEY) group over here. (GCHQ, DSD, GCSB, CSE)
- They have direct access into the NSA database right here.
- The Drug Enforcement Administration (DEA), Defense Intelligence Committee (DIA), FBI, CIA.
- All these people have direct access to all this data. (Google-like Search)
- BORTINGLEAD, SCORECARD, CONTENT PREPARATION ENVIRONMENT
- And it’s children’s data as well. It’s everybody on the line because they take it all. So it’s nothing. There’s no distinction. They don’t filter anything. It just captures everything.
- This is what General Alexander said in Menwith Hill Station a few years ago. He said, “All we have to do is collect it all.” And that’s what they’re doing.
The problem is, once you collect it all, and they have the impression or they give the impression that data is intelligence. When you collect more data, more intelligence. The point is you have intelligence when you understand the meaning of what you’ve collected.
“Bulk data kills people” is what I said to the UK when they were getting ready to pass the investigative powers bill, the bulk acquisition of data on everybody in the UK as well as everybody they can possibly get in the world. (38)
Nothing has changed. They’re still going out to more data, more people, more of an empire, and they still can’t figure it out.
Watch the full presentation for more.
Loads of Videos, with him (he was a whistleblower a decade before Edward Snowden), here’s a selection:
- 2022 Have we lost our right to free speech? (20min) (39)
- 2019 Open Forum Reflections of an NSA whistleblower (1hr) (40)
- 2016 TedX William Binney “An effective alternative to mass surveillance” (5min) (41) https://youtu.be/LufSe8-50-s
- 2015 “Whistleblowers: Stand Up For Truth” (2hrs) (42)
Wikipedia References
Wikipedia is mostly captured by these same agencies, thereby propaganda should be taken with a truckload of salt, but here are some Wikipedia articles on the various publicly disclosed Global Surveillance programs:
FBI Systems
Digital Collection System Network (DCSN/DCSNet)
FBI’s point-and-click surveillance system that can perform instant wiretaps on almost any telecommunications device in the US (72)
COINTELPRO
Series of covert and illegal FBI projects aimed at surveilling, infiltrating, discrediting, and disrupting American political organizations (73)
DWS-EDMS
Electronic FBI database; its full capabilities are classified but at a minimum, provides a searchable archive of intercepted electronic communications, including email sent over the Internet (74)
DCSNet
FBI’s point-and-click surveillance system (75)
Carnivore/DCS1000
FBI’s network sniffer (76)
Magic Lantern
FBI’s keylogger (77)
DITU
FBI unit responsible for intercepting telephone calls and e-mail messages (78)
Local Law Enforcement
Stingray (law enforcement agencies USA, UK, Canada, Saudi Arabia, UAE, and Turkey)
They use StingRay to force compatible cellular devices in a given area to disconnect from its service provider cell site and establish a new connection with the StingRay, and is used in several ways: firstly as communications interception and jamming device preventing the person from being able to use the phone, then, it can download the IMSI/identifier from each phone within a protest area, and after identifying the phones, locating and tracking operations can be conducted, and service providers can be forced to turn over account information identifying the phone users. (79)
Places
Pine Gap
Secret surveillance station close to Alice Springs, operated by the CIA, and jointly owned by Australia/USA. PineGap also contributes to XKEYSCORE among others (99) (100)
Southern Cross Cable
Australia, Fiji, Kiribati, New Zealand, and 3 states of US: Hawaii, Oregon, California
(101)
Fort Meade
Maryland, USA (102)
Utah Data Center
Intelligence Community Comprehensive National Cybersecurity Initiative Data Center, Utah, USA (103)
The Doughnut
GCHQ, England (104)
GCHQ Bude
UK eavesdropping centre in Bude/Cornwall, UK (105)
RAF Menwith Hill
Royal Air Force, England (106)
Bad Aibling Station
Bavaria, Germany (107)
Dagger Complex
US Military operating in Darmstadt, Germany (108)
Posts tagged: NSA
- Operation Mind-Control [Book]
- Sentient World – Militarizing our Bodies
- NSA Goal Is ‘Total Population Control’
- Former Child Actor Speaks Out About Illuminati Encounter
- Climate Science Q&A (Texti vs ChatGPT AI)
- Dr Robert Malone on who controls the world
- The REAL Anthony Fauci with Robert Kennedy, Jr.
- Tabletop Exercises
- Bilderberg Meeting June 2022
- COVID… from the Fringe [Gagged]

Site Notifications/Chat:
- Telegram Post Updates @JourneyToABetterLife (channel)
- Telegram Chatroom @JourneyBetterLifeCHAT (say hi / share info)
- Gettr Post Updates @chesaus (like fakebook)
Videos:
References